When testing for XSS I always begin with sending normal input characters to the web application in order to get a better understanding on how the web application functions, For example i just used the name chuck as my input to send over to the web application.
After sending hitting the submit button i received the following output from the web application.
After receiving the javascript message, I quickly did a view source from the browser in this case i'm using Firefox but any browser can be used when viewing the source of a web page.
As shown below in the source of the web application, My input of chuck has landed in the html context of the application right between the 'noscript' tags. which does not allow any JavaScript to execute.
Now that i know that my input will show up in html context, I understand that in order to get my custom JavaScript code to execute i'm going to have to break out of the 'noscript' tags and then inject my code right after breaking out. I can now begin to test for Cross Site Scripting (XSS) using the following characters below. Note: This is just the test string that i used you can use any characters to test to see what characters are allowed as input with the web application that your testing.
In order to break out of html tags im going to need the following characters " <>. As shown below the web application allows the input of the following characters -- <>" ' which is awesome because i know that this application is vulnerable to Cross Site Scripting (XSS).
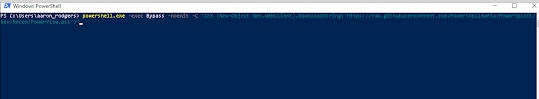
The following payload was used to break out of the noscript tags and injection my custom JavaScript
Well hopefully this tutorial will help someone realize that tools are not always needed in order to manually test for Cross Site Scripting (XSS).








No comments:
Post a Comment